A couple weeks ago, I was in California and met someone whose site was hacked, and he was completely unaware. I took on the clean-up of his site and set out to make sure that in the future his site was safe from falling prey again.
That process has really sobered me up, and made me realize just how vulnerable some of my sites have been.
The reality is that the best defense is actually having a defense, if you put your head in the sand, you’re gonna get swift kick in the ass.
The Downside Of Popularity
Just like driving a really common car, like a Honda Civic, there are a lot of vulnerabilities that come from using the most popular website platform. As more people utilize it, the more lucrative it can be for people to learn how to steal or exploit their availability. Since about 20% of sites now use WordPress, it makes it a bigger target for hacking.
Steps To Secure Your WordPress Site
According to Sophos Labs, they identify 30,000 new sites a day that are hacked! That’s a shocking number, but even that is incomplete as it only counts those identified as passing malware and not more subtle hacks that involve redirects or injecting link spam.
Here’s what I learned during the experience I mentioned above and from the helpful comments and contributions from several SEO experts on what you can do proactively to prevent it from happening.
Protect Your Login Page
One of the most common methods for hackers to gain access to your site is through brute force username & password guesses. There are a few options that can be used or combined to reduce the risk of having your password stolen.
Block Access to wp-login.php
The best way to protect your WordPress login page from brute force attacks is to block unauthorized users from even getting to the page in the first place. This will require some editing of your .htaccess file if you’re using Apache and your config file if using Nginx. Most hosts will allow this and if yours doesn’t, it may be worth considering a change.
The first and most secure method we will address is to limit access to your wp-admin directory by IP address. This method should only be used if you know what IP addresses you will be accessing the site from and those addresses won’t change on a regular basis. Typically this isn’t a problem, but it is one to keep in mind since you will block yourself from access if you’re not careful. Use the code below as an example for blocking access based on IP. The code also includes a section that unblocks certain files that may be needed by some of your plugins. If you’re using an Apache server, put this code in a .htaccess file within your wp-admin directory.
order deny,allow
allow from x.x.x.x
allow from y.y.y.y
deny from all
# Allow access to wp-admin/admin-ajax.php
Order allow,deny
Allow from all
Satisfy any
If you’re on Nginx, use the following code and replace x.x.x.x and y.y.y.y with your own IP addresses:
location /wp-admin {
deny 192.168.1.1;
allow x.x.x.x;
allow y.y.y.y;
deny all;
}
location /wp-admin/admin-ajax.php {
allow all;
}
Another method that will block access without the concern of being blocked if your IP changes would be to password protect your login page at the server level. This results in one more level of logging in, but is only a very minor inconvenience. You will want to start with generating a .htpasswd file and uploading it to your server; preferably not in a publicly accessible directory. Once you’ve generated that file and uploaded it to your server, and you’re using Apache, go ahead and add the following code to the .htaccess file in your wp-admin directory (or create the file if it doesn’t already exist). Make sure to update the path in the AuthUserFile line to match the location of the .htpasswd file you created.
# Protect wp-login
AuthUserFile /path/to/your/.htpasswd
AuthName “Login Required”
AuthType Basic
require valid-user
If you’re using Nginx, you can use the following code in your configuration:
auth_basic “Administrator Login”;
auth_basic_user_file .htpasswd;
}
If your host allows, you can pair this basic authentication method with fail2ban for Apache or Nginx and create rules where an abusive IP address gets added to your server’s firewall rules and is blocked for a specified period of time.
Plugin Options
Wordfence – This plugin serves as an additional firewall layer on your WordPress installation. There is an array of login security options available such as enforcing strong passwords and locking users out based on failed logins or the username they are attempting to use. For example, since you should never have “admin” as a username, you can add this to a list of usernames that will result in immediately blocking an IP address. This is frequently one of the first guesses hackers make in a brute force attempt and quickly shutting them out based on that simple rule is a good deterrent. Another handy feature is that you can suppress login errors to avoid tipping a hacker off as to whether or not a username is valid.
Login Lockdown – This is a plugin that can be added into WordPress which will block access to the site after a given number of failed login attempts.
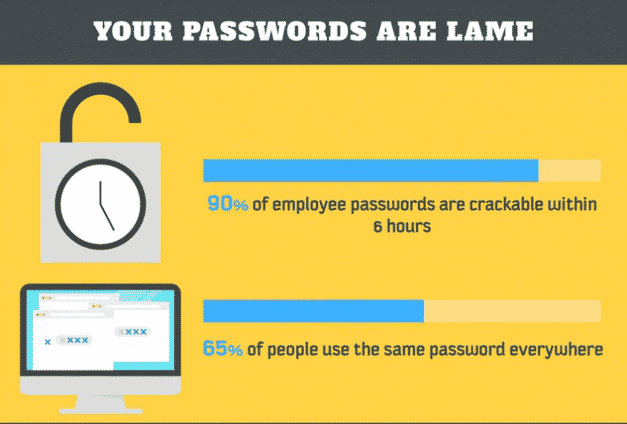
So what’s wrong with your password?
When we make passwords, we either make something that’s really easy to type, a common pattern, or things that remind us of the word password or the account that we’ve created the password for, or whatever. Or we think about things that make us happy, and we create our password based on things that make us happy. And while this makes typing and remembering your password more fun, it also makes it a lot easier to guess your password. Lorrie Faith Cranor
One solution is to use a longer pass phrase:
Here are some more common sense steps to further secure your password.
- Remove employee access to an application when an employee leaves.
- DO NOT write passwords down on paper.
- Don’t keep passwords in an unsecure spreadsheet or file folder.
- Use a pronouncable password, combining vowels and consonents to make something that flows off your tongue like “vadasabi”.
- Don’t use monkey, justin or love because they are among the most common words in the hacked password lists floating around the internet.
More Plugins = Less Security
It’s really tempting to say “is there a plugin for this?” unfortunately, that mentality can quickly lead to trouble. Take for example the huge fiasco that happened because of “Rev Slider”. This plugin was included in a slew of very popular themes but had a security vulnerability that ended up causing over 100,000 sites to be hacked!
That’s not the only plugin to cause problems. WP Super Cache and W3TC both had major security issues that made them vulnerable to being hacked. Fortunately, those were updated quickly but not every plugin gets the attention and maintenance needed.
Here’s what you should do to limit your plugin vulnerability:
- Eliminate un-used plugins and themes. There is no reason to open up your site to problems when you’re not even using them.
- Don’t use a plugin when you can do it yourself. According to Brian LaFrance “A good way to approach choosing a plugin vs. writing code for functionality is that a plugin should be used if functionality needs to remain identical even if a theme/design changes. If functionality is set up to fit in with a specific theme, that should be something built into the theme and not through using a plugin.“
- Update RELIGIOUSLY. Monthly is not enough. The more stale your plugins, the more vulnerable you are to exploits targeted at older versions.
Extra Steps To Improve WordPress Security




What Say You? Have Some WordPress Security Tips?
If you have some worthwhile security advice please add it in the comments. I’ll go ahead and add it to the post in an image too.